INDIA +91-9818398494, UAE +971-54-299-7566 | Philippines +63-91752-81177 | sales@gtisec.com | info@gtisec.com

WEB APPLICATION PENTESTING
A Web application (Web app) is an application program that is stored on a remote server and delivered over the Internet through a browser interface. Web services are Web apps process sensitive data such as user and financial information, which means they are frequently targeted by cyber criminals. As web apps become increasingly complex, the range of exploitable vulnerabilities is rising with time evolution.
Why do we perform Web application penetration testing?
Web application penetration testing is performed by using manual or automated penetration tests to identify the vulnerability, security flaws or threats in a web application. The tests involve using or implementing any of the known malicious penetration attacks on the application. The web application penetration testing key outcome is to identify security weakness across the entire web application and its components (source code, database, Web application firewall, front-end network or back-end network).
We can follow this process to perform web application penetration testing?
Penetration Testing Process
1. Scanning:
Web application scanning, also referred to as web application vulnerability scanning or web application security scanning, crawls a website for vulnerabilities within web applications. Scanning software is called web application scanners or vulnerability scanners.
2. Vulnerability Assessment:
Web Application Vulnerability Scanners are automated tools that scan web applications, normally from the outside, to look for security vulnerabilities such as Cross-site scripting, SQL Injection, Command Injection, Path Traversal and insecure server configuration.
3. Exploitation:
A website vulnerability is a weakness or misconfiguration in a website or web application code that allows an attacker to gain some level of control of the site, and possibly the hosting server. Most vulnerabilities are exploited through automated means, such as vulnerability scanners and botnets.
4. Reporting:
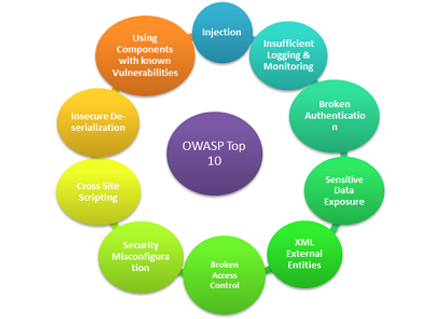
After the scan returns some results, the next step is to interpret the findings identified by the scanner. Results are displayed on the Dashboard in real-time, and you can start working on them even before the scan finishes. In addition, scan results can be exported to a comprehensive list of management and compliance reports, including reports for PCI DSS, OWASP Top 10, HIPAA, ISO 27001 and others.
Types Of Penetration Testing
Black Box Testing:
Black Box Testing is a Software Testing technique in which the tester doesn’t know the internal structure, design and implementation of the software application that is being tested.
White Box Testing:
White-box testing is a method of software testing that tests internal structures or workings of an application, as opposed to its functionality. In white-box testing an internal perspective of the system, as well as programming skills, is used to design test cases.
Gray Box Testing:
Gray Box Testing is a software testing technique which is a combination of Black Box Testing technique and White Box Testing technique. The internal structure, design and implementation is partially known in Gray Box Testing.






